
What Is Network Address Translation (NAT)?
Network infrastructure security has emerged as a major concern for businesses of all sizes at a time when digital transformation propels company expansion. Network Address Translation is one essential technology that supports both security and connectivity.
This mechanism, which is frequently shortened to NAT, serves as a simple firewall and permits several devices on a private network to share a single public IP address.
Let’s define network address translation (NAT), discuss its significance for contemporary businesses, and look at how Bluechip Gulf and other industry leaders use NAT in their firewall installations in Dubai to provide reliable network security solutions.
Table of Contents
What Is Network Address Translation (NAT)?
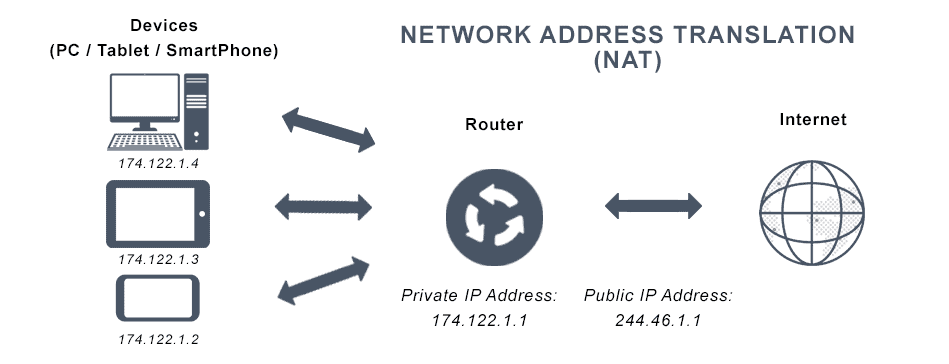
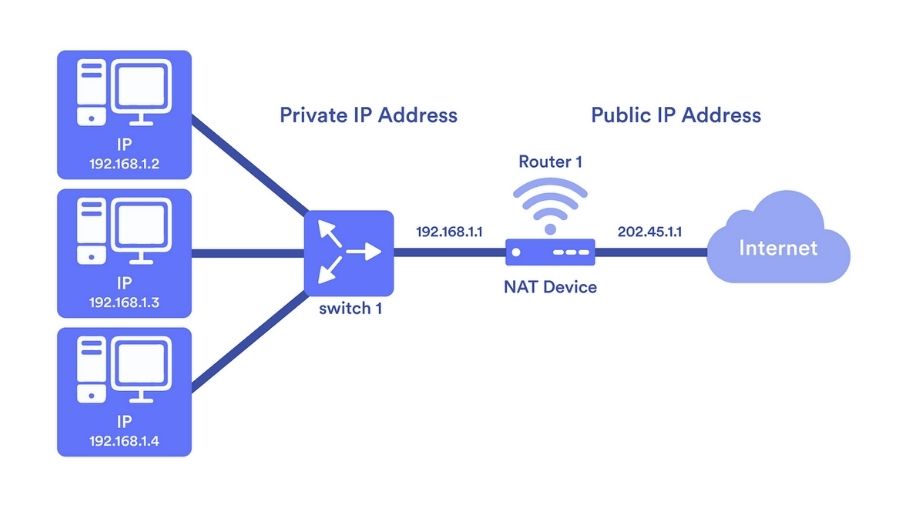
What is Network Address Translation? Fundamentally, NAT is a procedure that changes the IP address data in IP packet headers as they pass through a network gateway, usually a firewall or router. NAT preserves address space and improves privacy by converting private, non-routable IP addresses (like 192.168.x.x or 10.x.x.x) into public, routable IP addresses.
The NAT-enabled gateway records the session in a translation table and substitutes its own public address for the source IP when a device behind it establishes an internet connection. In order to ensure smooth two-way communication without disclosing internal network information, responses from external servers are subsequently mapped back to the original private IP.
Understanding the Basics of NAT in Network Security

By hiding the internal topology from outside parties, network address translation enhances network security in addition to IP address conservation. Malicious actors find it much more difficult to target devices on the private network directly since external hosts can only see the gateway’s public IP.
For many organizations, NAT serves as their first line of defense since it creates an implicit barrier that enhances more conventional security measures. Furthermore, NAT automatically rejects unsolicited inbound traffic since it necessitates stateful tracking of outgoing connections, thereby removing undesired connection attempts and minimizing the attack surface.
Why Network Address Translation Matters for Modern Enterprises
Cloud environments, hybrid infrastructures, and multiple locations are all used by modern businesses. Network Address Translation is essential for making it possible for –
1. Scalability – NAT enables companies to make the most of scarce public IP resources in the face of a shortage of IPv4 addresses.
2. Mobility – Without needing globally unique IP addresses for each device, remote and mobile users can connect safely using VPN gateways that make use of NAT.
3. Simplified Network Design – NAT manages address translation at the network edge, and private addressing schemes can be standardized internally.
4. Enhanced Privacy – Businesses protect device information and network architecture from outside reconnaissance by hiding internal IP addresses.
When implementing safe, effective networks that must change to meet changing business needs and legal requirements, these advantages are essential.
Key Types of NAT and Their Use Cases
Network address translation comes in a variety of forms, each suited to particular situations.
1. Static NAT – One private IP address is mapped to one public IP address via static NAT. Perfect for hosting services that need a constant public address, like mail or web servers.
2. Dynamic NAT – A private IP is mapped to a public IP selected from a pool using dynamic network address translation (NAT). Ideal for networks where not all hosts require simultaneous internet access and where there are more internal hosts than public addresses available.
3. Port Address Translation (PAT) – By distinguishing traffic through distinct source ports, Port Address Translation (PAT) converts several private IP addresses into a single public IP address. Entire corporate networks can share a single public IP address thanks to the most popular type of NAT.
4. NAT64 – By translating IP versions, NAT64 makes it easier for hosts that only support IPv6 to communicate with those that only support IPv4. vital when switching from IPv4 to IPv6.
Network architects can select the best strategy for applications ranging from basic internet access to intricate multi-site deployments by having a thorough understanding of these types.
Simplified NAT Configuration for Secure Networks

On a gateway device, configuring network address translation usually entails the following actions –
1. Define Internal and External Interfaces – Determine which interfaces are connected to the internet and the private LAN by defining the internal and external interfaces.
2. Create Address Pools – Set up a pool of public IP addresses for dynamic NAT.
3. Make Translation Rules – Either enable PAT for port-based translation or specify static or dynamic mappings.
4. Establish Access Controls – Use firewall rules to regulate what can enter and leave a system.
5. Monitor Translation Tables – To audit sessions, identify irregularities, and resolve connectivity problems, use logging and real-time monitoring.
These tasks are made easier by many contemporary firewalls’ user-friendly graphical interfaces and wizards. Simplified NAT configuration lowers the possibility of errors that could leave your network vulnerable, whether you’re running a global network or firewall installation in Dubai.
Enhancing Network Security with NAT Integration

Although NAT has built-in security advantages, network defense is improved by combining it with sophisticated firewall features –
1. Stateful Inspection – The firewall can implement granular policies according to connection context by monitoring session states.
2. Deep Packet Inspection (DPI) – Verifying payloads for malicious signatures guarantees that translated traffic is free of exploits and malware.
3. Application Awareness – Even if unauthorized services use allowed ports, modern firewalls are able to recognize and manage applications, blocking them.
4. Threat Intelligence Feeds – NAT gateways can automatically block high-risk sites thanks to real-time updates on malicious IPs and domains.
Organizations can achieve a multi-layered security posture that thwarts both sophisticated threat actors and opportunistic attackers by integrating NAT with these features.
How Bluechip Gulf Implements NAT in Next-Gen Firewalls

Known for providing end-to-end firewall installation in Dubai and beyond, Bluechip Gulf is a top Middle Eastern supplier of network and cybersecurity solutions. Bluechip Gulf uses Network Address Translation in its next-generation firewall deployments in the following ways –
1. Customized NAT Policies – Whether it’s protecting data centers, cloud environments, or branch offices, Bluechip Gulf’s professionals create NAT configurations that meet business needs.
2. Integrated Security Suites – To guarantee thorough threat protection, each firewall has intrusion prevention, antivirus, and web filtering modules in addition to the standard NAT.
3. High Availability and Scalability – Bluechip Gulf uses failover and clustering techniques to ensure that NAT services continue even when the network is overloaded.
4. Centralized Management – Network managers can monitor traffic, control NAT rules, and distribute policy updates amongst dispersed firewalls all from a single window.
5. Professional Support and Optimization – Bluechip Gulf’s managed services guarantee that NAT configurations stay resilient against new threats, from the first firewall installation in Dubai to continuous performance tuning.
Bluechip Gulf helps businesses maintain safe and robust network architectures that are suited to the particular requirements of the digital age by utilizing network address translation in combination with state-of-the-art firewall technologies.
Conclusion
Address-sharing is only one aspect of Network Address Translation. It is a fundamental security control that maximizes limited IP resources while protecting internal networks from direct exposure. Organizations can use Network Address Translation (NAT) to create safe, scalable, and controllable networks by first learning what it is, then investigating its different varieties, and finally implementing best practices.
You can rely on Bluechip Gulf to provide professional NAT implementations and comprehensive cybersecurity solutions that keep your company safe around the clock, whether you’re planning a firewall installation in Dubai or strengthening your global infrastructure.
Also Read: What Is Remote Access Trojan (RAT)?





