
SOC Services Dubai – Protect Your Business 24/7 In 2026
SOC Services Dubai offer 24/7 cybersecurity monitoring, threat detection, incident response, and risk management using expert analysts and advanced tech (like SIEM/AI) to protect businesses from cyberattacksAs Dubai develops into a world-class digital technology hub, the business environment will continue to grow more complicated. In 2026, we are moving away from model defense perimeter approaches and toward proactive artificial intelligence (AI) based security models. For any business that operates in the UAE, providing 24/7 security is no longer an option but should be a best practice to ensure compliance and survival.
It describes how the Security Operations Center (SOC) is critical in providing protection today with state-of-the-art SOC services in Dubai, particularly through providers such as Bluechip Computers LLC.
Table of Contents
What is a Security Operations Center (SOC)?

A Security Operations Center (SOC) operates as a centralized hub that connects individuals, processes, and technologies together to provide a continuous assessment and ongoing improvements in an organization’s cybersecurity posture. As being synonymous with the brain of your organization’s cyber protection system, it is actively watching over the organization’s systems, including the internal networks, the host devices (servers), and the application activity in an always-on approach for indications of cyber intrusion.
SOC services provide the following key functions –
1. Prevention & Detection – Utilizes proactive log reviewing and network activity monitoring to identify potential intrusions and possible threats prior to disruption.
2. Occupational and Triage – Investigate all Security Alerts, filter false positives from true positives, and promote the prioritization of true negative alerts by an organization according to the level of severity.
3. Incident Response – Respond instantly to the initiation of an Information Security incident and, as required, contain, remediate, and resolve the event per the organization’s information security incident response plan.
4. Recover & Remediate – Restore the relevant Information Systems back to their intended original state from exposure due to the occurrences of an Information Security incident. Implement the necessary information security repairs, updates, and/or patches to prevent future occurrences.
5. Threat Hunting – Proactively searching for threats that have bypassed or evaded existing security tools or processes. Perform Threat Hunting as an organization through methods and processes more advanced than those of its current inventory of security tools.
Why 24/7 SOC Services are Non-Negotiable in 2026

The cybersecurity threat landscape in the SOC UAE region is described by speed and complexity. Cybercriminals use international, usually launching attacks outside of normal business hours (nights, weekends, and holidays) when corporate IT teams are generally offline.
The Benefits of Continuous 24/7 Monitoring –
1. Rapid Response Time (MTTR) – The SOC team’s swift response time (MTTR) enables them to react immediately when an alert goes off. This significantly decreases the attacker’s potential for undetected “dwell” time, therefore decreasing the chance of suffering data loss or system damage.
2. Global Threat Intelligence – Global threat intelligence feeds are included as a part of all SOC services. As a result, SOC services offer an external source of intelligence that can help protect against fast-emerging threats globally, such as ransomware variants or zero-day vulnerabilities. Shifts security from one of reactive firefighting to that of a proactive defense.
3. Cost Efficiency – Outsourcing your SOC services Dubai is much more cost-effective than establishing an in-house SOC. An internal SOC will require a large capital investment in technology, having 3 tiers of analysts (Tiers 1, 2, and 3), and purchasing and equipping them for training. By outsourcing to SOC services providers, your organization can reduce both operational expenses and resource strain on the internal IT staff.
4. Regulatory Compliance – The requirement for your organization to continuously collect and monitor logs and provide detailed reporting on incidents will help meet the UAE’s stringent regulatory requirements, such as the information security regulations of Dubai ISR and the personal data protection law of the UAE PDPL, which can result in significant regulatory fines if they are not complied with. Additionally, the provision of this type of information demonstrates your company’s commitment to providing excellent data security to its stakeholders.
The Modern SOC – AI, Automation, and Zero Trust
As a result of ongoing technological advances, 2026 effective SOC services are vastly different from traditional manual monitoring center setups, due to the ability to integrate AI-based capabilities to address the growing threat of AI-based attacks.
A. Key Technologies Driving Modern SOC UAE
1) SIEM (Security Information and Event Management) – SIEM serves as the central point from which log data is collected, aggregated, and analyzed for all endpoints, cloud assets, and network data, which allows the identification of patterns that signal a potential breach. Modern SIEMs are extensively augmented using AI capabilities.
2) SOAR (Security Orchestration, Automation, and Response) – SOAR serves as an automation tool that allows SOC to eliminate repetitive processes (for example: triaging alerts, enriching alert data, isolating infected endpoints) from the SOC. This allows for significant reductions in the time needed to respond (Mean Time to Respond – MTTR) to an alert and allows human analysts to spend time working on advanced investigation and strategically hunting for threat actors.
3) XDR (Extended Detection and Response) – XDR provides a holistic view and protection of unified security across all layers (endpoints, cloud, network, and email) to provide an SOC with the ability to see the entire “kill chain” of an attack.
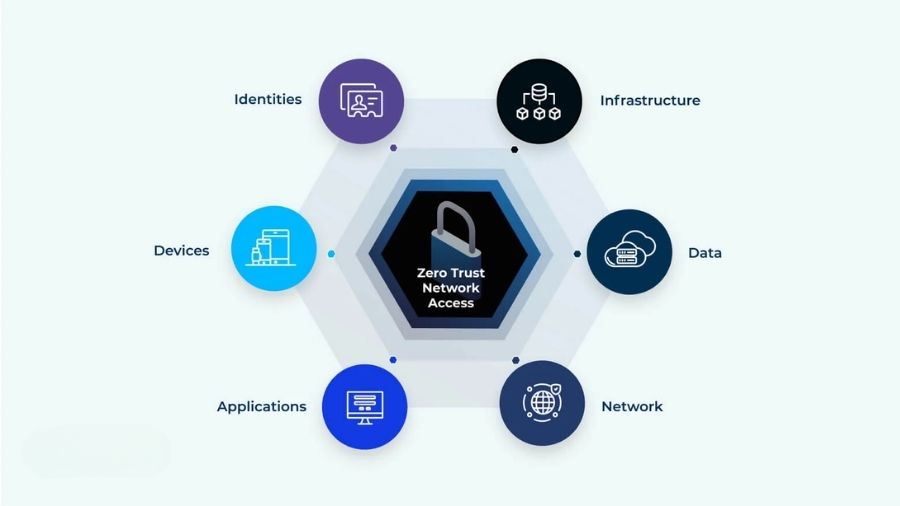
B. The Zero Trust Security Model
A Zero Trust architecture, in particular, defines how SOC services in Dubai will operate. That means no user, application, or device, inside or outside the network, is trusted by default. Each time a user tries to access the SOC, the SOC will continuously verify who they are and check their “least privilege” rights before allowing them access. The SOC will monitor all access attempts and enforce the Zero Trust architecture as part of its ongoing operations.
Choosing a Reliable SOC Partner in Dubai

Most companies, especially small and mid-sized businesses (SMEs), will find that the SOC-as-a-Service model is the most effective means of implementing a strong SOC model. SOC-as-a-Service is an arrangement between an organization and a managed security service provider (MSSP) where the MSSP monitors the organization around the clock and provides support to ensure the organization remains compliant with regulations.
When looking to establish a SOC Services Dubai partnership, businesses should consider the following –
1. 24/7/365 Coverage – Critical for detecting attacks outside of regular business hours, lowering dwell time, and ensuring prompt containment of attacks.
2. Local Expertise/Compliance – Partner should possess local expertise regarding local laws (like Dubai ISR and NESA) and information regarding local threats, not just global information regarding threats.
3. Technology Stack – Look for use of next-generation technologies (e.g., AI, ML) for SIEM, XDR, and SOAR platforms in order to properly deal with modern-day, fast-paced attacks.
4. Incident Response SLA – Should clearly state and state by contract the amount of time it takes to discover (MTTD) and resolve (MTTR) critical incidents.
5. Data Sovereignty – Providers must offer data residency and sovereign operations for sensitive data to maintain compliance with regulations. All critical data must remain in the UAE.
Bluechip Computer Systems LLC – provider of SOC services in Dubai

Emerging firms like Bluechip Computer Systems LLC illustrate the type of specialized, locally focused knowledge that is in demand in the UAE. Bluechip is a full-service provider of SOC services in Dubai. Companies such as Bluechip provide –
- 24/7 Threat Monitoring – Continuous monitoring of all aspects of a company’s network, systems, applications, etc., to identify potential threats.
- Real-Time Alerting & Analysis – Using advanced software tools and analytics to detect anomalous activity as soon as possible.
- Proactive Incident Response – A dedicated team responsible for taking immediate action to contain a security breach (isolate affected systems, eliminate the threat) and to expedite recovery from a breach.
- Compliance Support – Detailed reporting and insight to assist with compliance requirements imposed by local and international regulations.
Through partnering with an organization that provides customized and ongoing SOC UAE services, organizations can access highly skilled knowledge in the area of cybersecurity that they would normally be unable to afford or build.
The Future – A Proactive Defense Strategy
As we approach the year 2026, cybersecurity will need to take on an entirely new approach to the industry. SOC services are beginning to evolve into something other than organizations that react after an incident occurs by providing these services. SOC services are now looking for threats and predicting when they will happen so they can be proactive with their reporting.
For any company doing business in Dubai, establishing a fully-equipped, 24/7 Managed SOC solution will serve as the best way to mitigate the increasing risk from ransomware, data loss due to data breaches, and today’s high-tech phishing attacks while keeping your organization secure and compliant in the rapidly evolving digital economy.
Also Read: Top Email Security Threats In 2026 And Cloud Protection Solutions








